Today, companies, both large and small, are investing in eCommerce. It’s hard to find even a primarily brick-and-mortar store that doesn’t have an online presence.
But in many ways the Internet is still like the Wild West. There are tons of individuals seeking to rob others. And just like bandits of the past, modern hackers often target small business owners and everyday entrepreneurs.
According to Verizon, just last year over 40% of data breach victims were small businesses.
The danger is very real.
But what can a small company do if it doesn’t have the resources to hire a cybersecurity specialist or even a general-purpose IT guy?
Exactly what a Western movie protagonist would do: take their safety into their own hands.
On this list, you’ll find 7 tips on how to protect your small business from cybersecurity threats. The best thing about them is that anyone can implement — no tech skills required.
1. Restrict Employee Access & Permissions
The sad truth about data breaches and other cyberattacks is that they are very often facilitated by company employees.
In most cases we’re not talking corporate sabotage — it’s usually just simple human error. In fact, IBM found that human error was the cause of 95% of data breaches.
There are many ways in which an employee may compromise your cybersecurity:
- Opening suspicious emails
- Browsing dangerous websites
- Clicking malicious links
All three of the above can be part of a phishing attack.
What is phishing?
Phishing attacks are counterfeit emails that look like they come from a trustworthy source. Often phishing emails are sent to individual employees at a specific company as a sneaky way to steal their passwords and login information.
What do phishing attacks look like?
Here’s a real example of a phishing email and landing page, designed to look like it came from GoDaddy, so cybercriminals can steal your password:
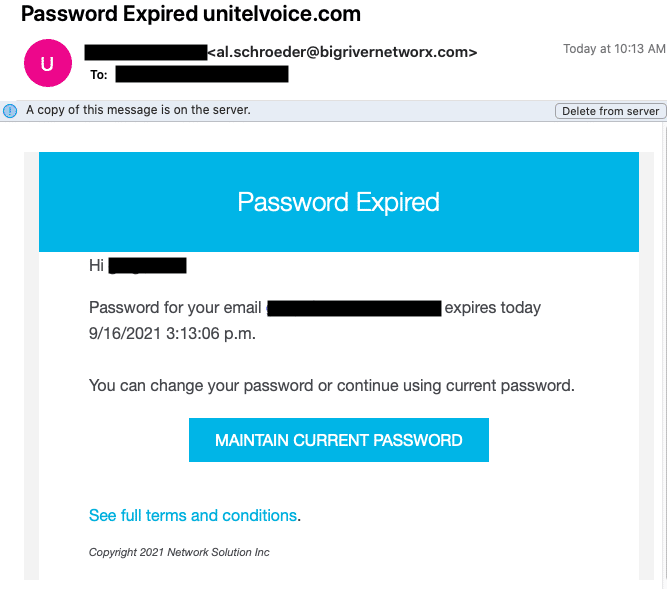
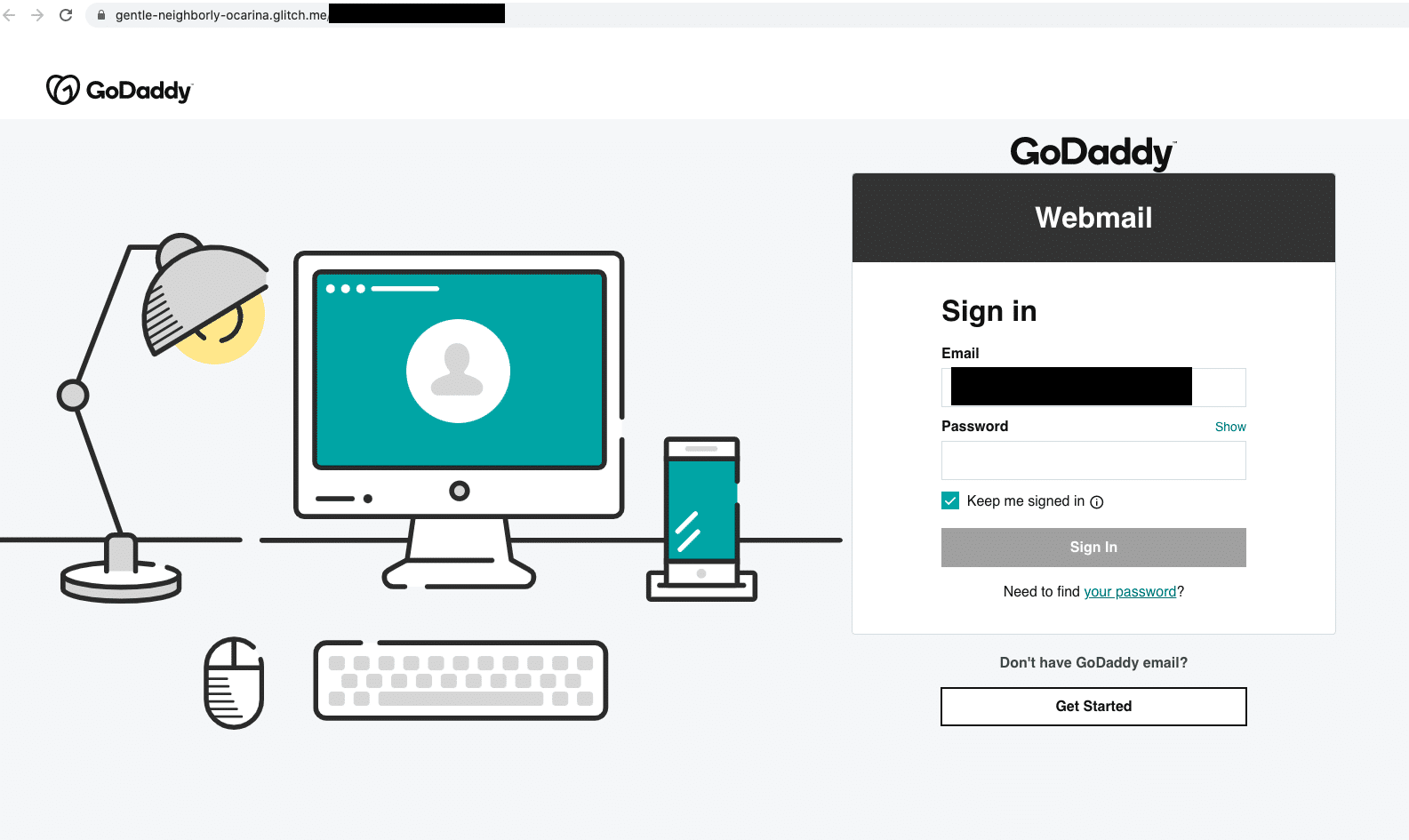
So what do you do?
Warn your employees about these kinds of attacks and regulate their internet access. It just takes one malicious website or files to endanger your company’s cybersecurity. In some cases, literally just one click.
This is where getting an OpenDNS service comes into play.
OpenDNS services come in free and paid (corporate) versions. They allow you to set simple restrictions on what websites can and can’t be accessed from your network.
The most convenient thing about an OpenDNS service is that it already has lists of dangerous websites divided into categories you can enable or disable with a click. And setting one up isn’t hard.
Additionally, an OpenDNS service allows you to block sites you feel may distract your employees from doing their job such as gambling, video services, social networks, etc.
But that’s entirely up to you.
2. Use A Virtual Private Network
This applies to any eCommerce business but it’s especially important if your company employs remote workers.
A virtual private network, or a VPN, is a technology that encrypts data you send over the internet so that it can’t be read by snooping third parties.
When you store information about your customers and regularly process payments, VPNs can go a long way in keeping your data safe from hackers.
There are a lot of VPN providers out there all offering different features, speeds, security, and other parameters.
Here’s a great place to find one that works for you.
3. Perform Penetration Testing
To continue the Wild West analogy, some hackers wear black hats, and some wear white.
The black-hat hackers are the bad guys who seek to get into your system by exploiting human factors, software vulnerabilities, and other weak spots for their personal gain without your permission.
As for the white-hat or ethical hackers, they want to do the same thing… only because you ask and pay them to.
It may sound a bit counterintuitive to pay someone to hack your system, but it really is an indispensable way of testing how strong your network is.
Known as penetration testing, this strategy is like a fire drill for your organization: it lets you see what is lacking in your cybersecurity setup and take measures to fix it.
Unlike a dedicated security team, you must pay for upkeep, and pen testers will be your one-time contractors. Of course, as the cybersecurity landscape is constantly changing, you may want to run these tests every once in a while – once a year is good enough, and once every six months is great.
4. Secure Your Premises
Sometimes, software-only measures are not enough to fully protect your company.
Depending on what kind of business you run, your office may see a lot of visitors every day. And if you are being targeted by cybercriminals, stepping foot in your place of business is a good way for them to assess how well you are protected.
For example, it could be as simple as an employee writes down their password on a piece of notepaper and leaves it on their desk. Not only does it allow a potential malefactor to snap a quick photo of it while nobody is looking, but it also tells them your company’s attitude towards cybersecurity.
It doesn’t mean, of course, that you should turn your office into Fort Knox. However, certain simple precautions must be taken.
In general, your visitors should not be able to see or hear anything that does not directly relate to their specific case.
You can achieve that by doing a little restructuring of your working space and making sure that sensitive company and customer data does not lie unattended in broad daylight.
5. Backup Your Data
One of the most devastating cyberattacks for businesses and nonprofits alike is ransomware.
It is a type of malware that gets installed on a computer and blocks the user’s access to all the programs and data stored on that device.
The purpose of it is to extort money from the victim for unblocking their computer. Of course, there’s never any guarantee that the hacker will keep their promise once paid.
For a company, losing access to its business data often means losing its very ability to conduct business.
If you can’t see, for example, the deliveries you have to make today and the addresses of the clients you have to deliver those items to, you won’t be able to satisfy your customers’ demands, ruining your day and reputation.
This is why you should keep regular backups of your important data on a device not connected to the network and the internet.
The best way to do it is by using an external hard drive. It connects to a computer via the USB port, can store terabytes of information, and can be encrypted with BitLocker, a powerful program preinstalled on modern Windows.
Since it is basically a USB flash drive, it doesn’t have an internet connection so even if your system gets blocked by ransomware, the hard drive won’t be affected by it.
6. Establish A Password Policy
Snooping passwords or obtaining them via malicious links and emails are not the only way hackers can get your employees’ credentials.
There is also a method called brute-forcing.
Brute-forcing involves hackers literally trying to guess the password that would get them into the system.
Of course, they aren’t doing it all by themselves. Instead, they are helped by artificial intelligence and machine learning algorithms, which make the process much quicker.
However, to break a long and varied password this way, even AI must take a couple of million-year-long vacations. If you use special symbols, letters, and digits, you are safe from brute-forcing.
The thing is, not many people use complex passwords. Most passwords are terrible.
If your company has any employees, chances are, at least some of them are using weak passwords to get into the system.
It is up to you to stop this dangerous practice.
You have to ensure that all your workers know and understand the importance of using strong passwords.
To guarantee compliance, you should be precise when delivering this point to them. Specify the number of symbols required (at least 12), the need for capital and lower-case letters, digits, and symbols like #, &, %, etc.
7. Conduct Cybersecurity Awareness Training
It’s a good idea to take the above tips and conduct an in-house cybersecurity training program, so your employees understand the threats and how to protect against them.
Yes, it costs some time and money, but nowhere near as much as a data breach.
Everyone working for you should be involved in this training – without exceptions. That, of course, includes you.
Remember: following these recommendations will not make your company 100% immune to all cyber threats. It will, however, make you far more resistant to them and able to recover faster if an attack happens.
Editor’s Note: This article is part of the blog series Run Your Business brought to you by the marketing team at Unitel, the virtual phone system priced and designed for startups and small business owners.